By Prasad Kunchakarra | April 10, 2019
Why Application Security Configuration Management is Essential and Economical
Expanded Cyber Kill Chain Model Analysis
Traditionally, cyber security programs are more focused on boundary defense controls. In this approach, IT organizations fail to take a holistic view of the most essential controls required to prevent an adversary from achieving his goal. A holistic analysis using an Expanded Cyber Kill Chain Model can achieve essential and economical application security configuration management. In this blog, a systematic analysis is performed to show the importance and economics of an application security configuration management solution.
What is Application SCM?
Security Configuration Management (SCM) is a process, by which the security configuration baseline of IT components is formalized and subsequently verified against the actual state of security configurations. An Application Security Configuration Management (ASCM) can be defined as a configuration management process where activities focus on your application, its data, and its interaction with other asset classes.
Brief Overview of Cyber Kill Chain Model
Developed by Lockheed Martin (from an external adversary perspective), the Cyber Kill Chain framework is used in the identification and prevention of cyber intrusions activity. The model identifies the steps an adversary will take to achieve their objectives. The seven steps of the Cyber Kill Chain enhance visibility into an attack and enrich an analyst’s understanding of an adversary’s tactics, techniques, and procedures.
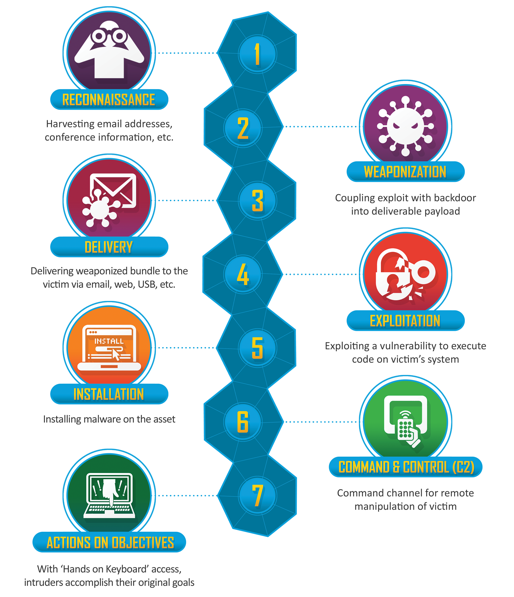
Legacy Cyber Kill Chain Model
Expanded Cyber Kill Chain Model
The legacy Kill Chain model is excellent for analyzing external attacks, but does not work effectively for internal threats. In today’s environment, every attack is an internal threat – once an outsider has breached the perimeter, they have effectively become an insider. An expanded Kill Chain model was presented by Sean T. Malone in a Blackhat conference in 2016. It can be depicted as follows:
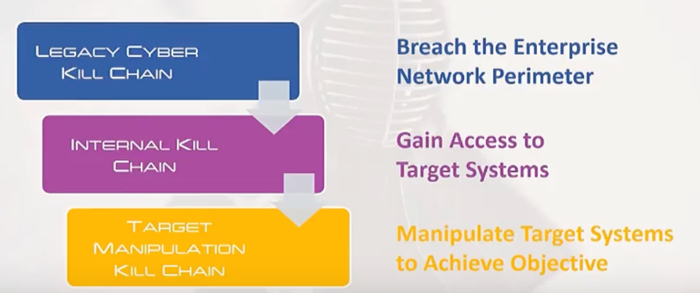
Expanded Kill Chain Model Overview
The expanded model includes two additional chains that adversary must go through, prior to achieving his objectives. A detailed view of these chains is shown below:
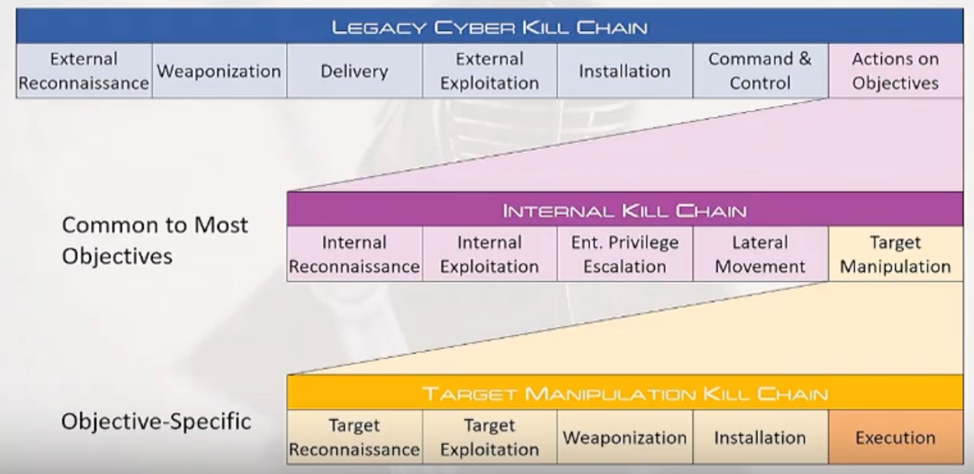
Expanded Kill Chain Model Details
As shown above, the external kill chain continues into an internal kill chain, followed by a target manipulation kill chain. If an adversary is an internal actor, then the legacy external kill chain is bypassed However, If the adversary is external, once he breaches the boundary of the defense, then the treatment of internal and external adversary efforts should be identical. This means that the organization does not need to focus on whether the adversary is internal or external, but on configuring controls appropriately at every stage of the Expanded Kill Chain model.
How can Application Misconfigurations Make Adversary’s Goal Accomplishment Easier?
If an organization has failed to pay attention to their application security configurations, the following expanded kill chain model scenario may occur:
- An adversary gains access to an application server where the application properties are misconfigured:
- The requirement is for the application to use an SSL cert-based authentication – instead the application is misconfigured to use plain text credentials.
- The privileges for this user should have been read only privileges – instead they are misconfigured in the database to have system access privileges. This may give an adversary the ability to escalate their privileges and to move around freely within the database to discover sensitive data.
Application Security Configuration Validation is Essential Security Hygiene
The Expanded Kill Chain Model analysis indicates the following:
- Application configurations along with their touchpoint systems, especially where the data is stored, need to be verified to detect any misconfigurations.
- The applications should have an associated business context, and this must be visible to the security analyst so that the impact associated with any breaches can be immediately understood.
Gaps in Security Vendor Tool Offerings
Our current market survey for the cyber security vendor offerings have shown the following deficiencies:
- Application inventory is not identified
- Application configurations are not verified
- Role-Based Access Control verifications required for the specific application cannot be verified
C2VS Addresses Application Security Configuration Management Gaps:
The Capitis team has developed the C2VS solution specifically to address these gaps. We consider addressing these gaps to be foundational in nature, and essential in maintaining security hygiene. The organization’s security team should take an application-centric view to prevent lateral movement of the adversary and escalation of privileges, as well as making it easier to detect adversary movements. The following diagram shows how the strength of defenses factors into the adversary’s economic considerations.
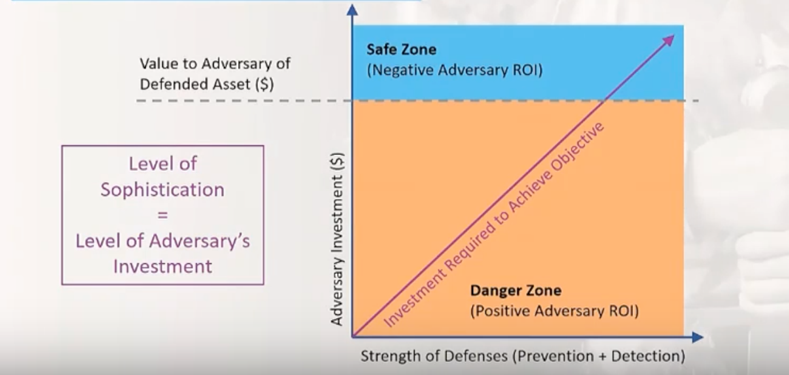
Economics of Strength of Defense
An organization can eliminate deficiencies in application configurations by identifying misconfigurations with respect to the application and its associated touchpoint configurations. With proper defense configurations at the application level, the adversary investment to reach and exploit the target becomes prohibitive. We strongly recommend implementing an effective application security configuration management solution as an essential element of the holistic cyber defense strategy.
Reference:
Using an Expanded Cyber Kill Chain Model to Increase Attack Resiliency by Sean T Malone. www.seantmalone.com, Blackhat USA 2016 conference presentation.
URL: https://www.youtube.com/watch?v=1Dz12M7u-S8&feature=youtu.be
About the Author
Prasad Kunchakarra is the CEO and Founder of Capitis Solutions Inc. He has over 15 years of experience in architecting and implementing secure platforms both for Government and commercial clients.
