By Prasad Kunchakarra | March 26, 2019
What is the Role of Configuration Management in Defense in Depth Strategy?
A defense in depth strategy for implementing security controls recommended by NIST 800-53 or other frameworks requires comprehensive security controls throughout the data, application, network and infrastructure layers. I would like to capture some of my thoughts on prioritizing the tasks related to defense in depth strategy at government agencies and other highly regulated industries such as financial institutions.
A decade ago, most security efforts were focused on implementing boundary controls at network and infrastructure layers. Very little attention was paid to the data and applications. With the increase in threats posed by external and internal actors, information security teams at government agencies and other highly regulated sectors are now implementing controls for protecting data-at-rest and data-in-motion through encryption. In addition, penetration testing and vulnerability management has matured considerably. However, we do not see the same level of attention directed toward the hardening and configuration management of applications and vendor products such databases, application servers and web servers. A 2018 Gartner report on “Cloud Protection Hierarchy” identifies hardening and configuration management as the most critical element of a defense in depth strategy for cloud workloads.
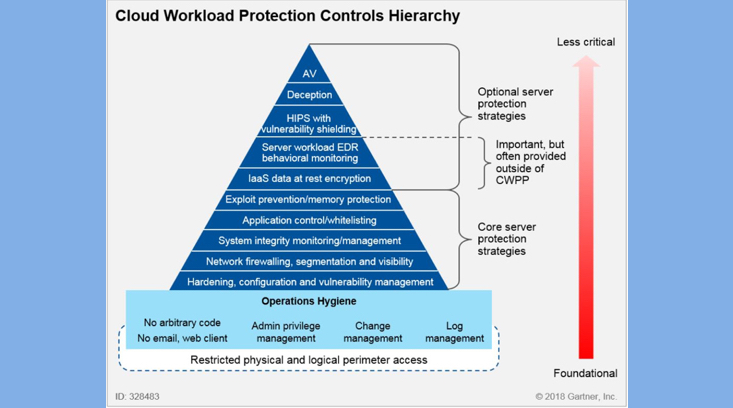
It is to be noted that the Center for Information Security (CIS) has published clear and actionable benchmarks for many vendor products including Oracle RDBMS, Microsoft SQL Server, Apache Tomcat, and other widely used enterprise software products.
During a recent engagement with a financial customer we were able to automate the hardening of their databases and application servers using established security standards coupled with baseline definitions customized to their unique security requirements. In addition, we implemented automated independent compliance tests that continuously monitor and identify any mis-configurations over time. By mapping these controls to NIST 800-53 controls we expedited compliance audits and ATO (Authorization to Operate) processes. We have successfully implemented solutions using our C2VS framework that has saved thousands of hours of manual efforts involved in collecting the evidence for compliance audits and production release gate reviews.
We recommend that Government Agencies and other highly regulated industries automate hardening of their vendor furnished products and perform independent compliance verification tests as a pre-requisite to a defense-in-depth strategy.
About the Author
Prasad Kunchakarra is the CEO and Founder of Capitis Solutions Inc. He has over 15 years of experience in architecting and implementing secure platforms both for Government and commercial clients.
