By Prasad Kunchakarra | April 4, 2019
Modern Application Architecture and Why Security Configuration Compliance is a Challenge
It is an exciting time to be an IT professional because innovation in the industry is driving the economies of nations. Even traditional industries like hospitality and transportation are being radically transformed with business models that leverage cloud-based software platforms and architectures. Microservice adoption and external solutions provided as services have been key to this transformation. Microservices, by breaking applications into many smaller re-usable services, enable much faster – even daily – product release cycles. PaaS, IaaS and SaaS solutions mean that you no longer need to build everything yourself. Your solution can quickly utilize these external resources largely through configuration. And yet with arrival of these powerful technologies, so too has come a much more complicated security problem. There are no longer small, well-defined boundaries around monolithic applications. There are many more internal and external entities accessing and moving data across the wire, and traditional security tools with a perimeter focus leave many blind spots. A compliance solution needs to be designed with an understanding of your application and how it is configured in order to secure your sensitive data.
Traditional Monolithic Application Versus Microservices
The application architecture of IT systems is continuously evolving to meet the needs of rapid innovation. During the last fifteen years, the The application architecture of IT systems is continuously evolving to meet the needs of rapid innovation. During the last fifteen years, the application architecture has evolved from a single monolithic executable to many decoupled microservices. The following diagram illustrates the differences. A microservice architecture is characterized by many deployable components each with their own datastores talking to each other over the wire. The data and the application logic is distributed at many places, and the data movement is much higher compared to a traditional n-tier approach. The result is a much greater attack surface for security professionals to defend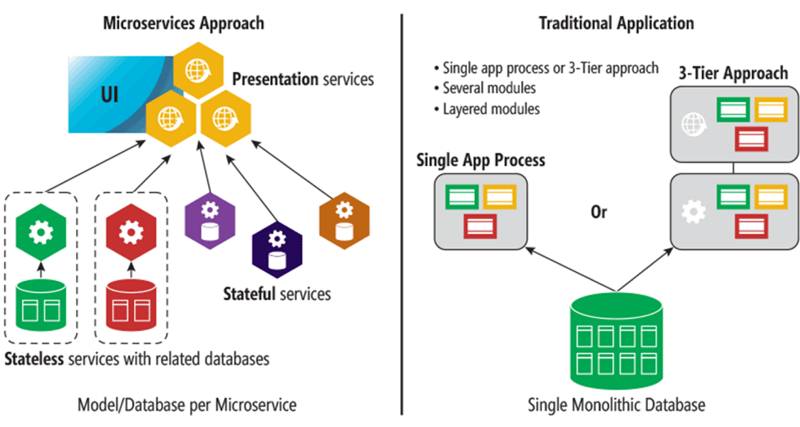
Modern Applications Depend on Several Microservices both Internal and External
During the last fifteen years, the world has become digitally connected. The reality is that software as a service has become a utility like any other (e.g. power and water). Most modern applications are now assembled from several internally developed microservices, and integrated with external third-party services through APIs. Each service invoked by an end-user could interact with over a dozen other services to accomplish a single task – Every one of these interactions is a potential vulnerability.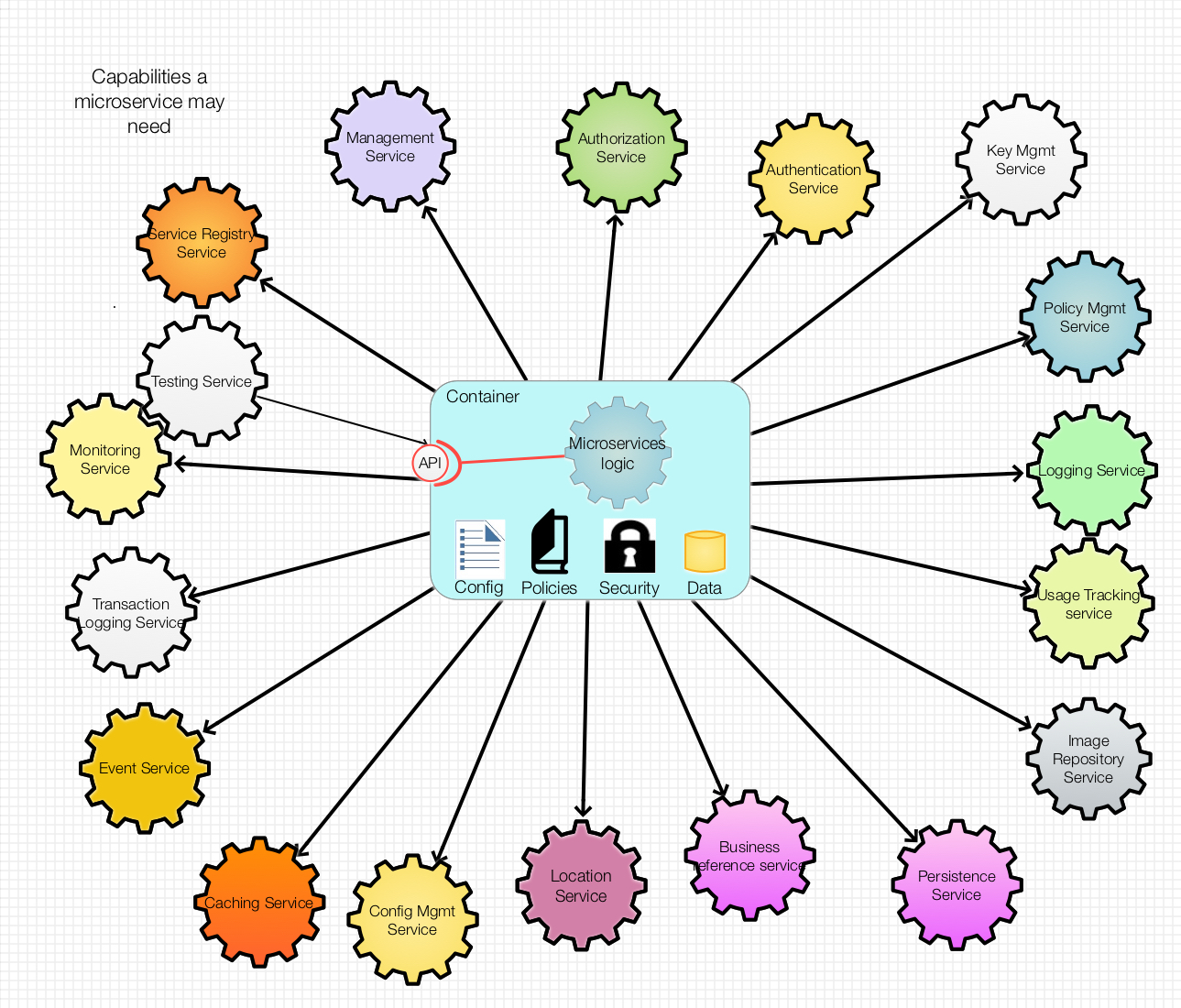
Proliferation of Microservices Configurations Including Security Configurations
The number of configurations that a single application must deal with is exploding. Capitis recently developed a serverless application to process streaming data and show real time dashboards on AWS; there were approximately 100 configurable parameters that could be tuned for each AWS environment. Out of these 100 parameters, 10-20 percent were related to security configurations, such as: security groups, IAM policies, encryption keys, user names and passwords, etc. The multi-tenancy of a platform further complicates the security controls and its configurations, where each client may require their own instance with its own set of configurations. As the number of configurations for an application increase and rapidly evolve, the chances for misconfigurations increase exponentially. The potential for sensitive data leaks arising from external or internal threats could be substantial if the misconfigurations – especially those related to security – go undetected.
Application Security Boundary and Blast Radius for Security Controls is Increasing
The defense in depth model was developed when most of the applications and data were hosted in one or two data centers owned or leased by the enterprise. The application boundaries were much smaller and localized. Over time, we have seen that insider and outsider threats have become equally important, and focusing security controls at the boundaries of your network and infrastructure is not enough. Security experts are questioning the relevancy of the organization’s network as a boundary. Instead, we should be thinking about the security boundaries in terms of applications and the number of associated services. The focus needs to be redirected to inside the perimeter where the application vulnerabilities lie.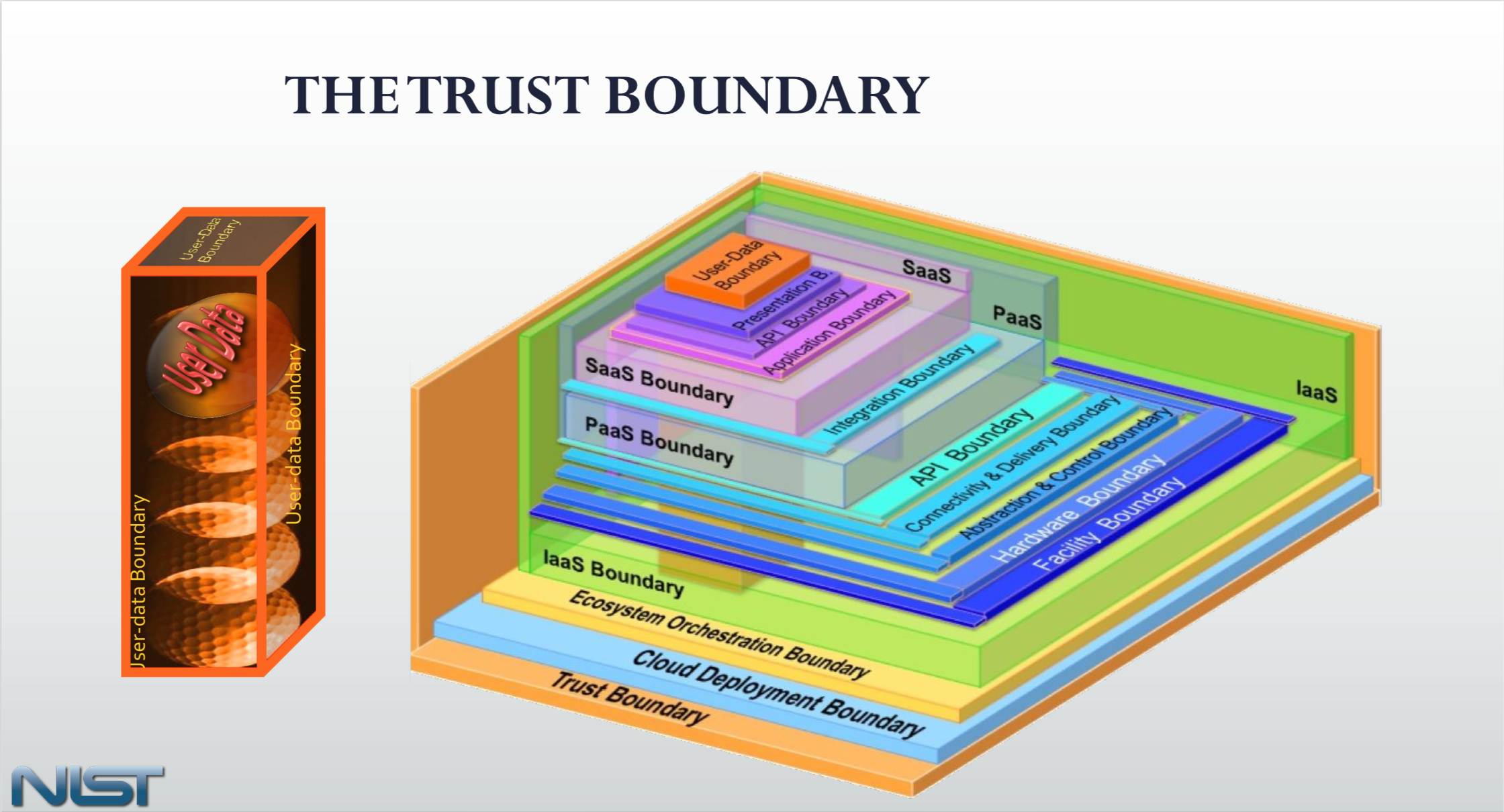
Traditional Security Tools Focus on Network and Infrastructure and Leave Many Blind Spots
The traditional security compliance tools focus primarily on infrastructure and network threats, and leave blind spots when it comes to the application security configurations. Even the cloud governance and configuration management solutions, such as Divvy Cloud, CloudWare, CloudCheckr, Cloud Conformity, Cloud Health, and AWS Config, can only focus on cloud resource configurations, but not the actual custom applications and their configurations related to utilizing the cloud resources.
Compliance Solution Should Understand Your Application
Based on our deep background in modern application architectures and security needs, we developed C2VS, an independent security configuration compliance solution that can be customized to the needs of your applications based on your organizational standards and risk profile. The pluggable architecture of C2VS enables easy configuration of security validation checks with extendable risk/impact metadata to meet your custom application and reporting needs. Capitis has developed this solution based on our experience in solving real world problems, particularly in highly regulated industries such as finance and government agencies. By using C2VS, we are able to identify and prioritize misconfigurations and their root cause so that the issues with the highest impact can be remediated immediately. Security teams are empowered to understand the root cause of the problem instead of engaging a multi-disciplinary team. At our customer sites, we are able to reduce 1000’s of hours of manual compliance checking to a couple of hours using automation accomplished through C2VS.About the Author
Prasad Kunchakarra is the CEO and Founder of Capitis Solutions Inc. He has over 15 years of experience in architecting and implementing secure platforms both for Government and commercial clients.
